kb890830 – what is it? A secret code? A product key? A random string of characters? This seemingly innocuous alphanumeric sequence could hold the key to unlocking a hidden world of information, or it might just be a meaningless jumble.
We’ll delve into the depths of its potential meanings, exploring its structure, comparing it to similar codes, and even imagining its hypothetical applications. Get ready to crack the case of kb890830!
Our investigation will span various analytical approaches. We’ll dissect the string itself, examining patterns and potential mathematical or logical interpretations. We’ll then look at the broader context, considering potential industries and scenarios where such a code might appear. Finally, we’ll address potential security implications and future considerations, painting a complete picture of this enigmatic sequence.
Initial Investigation of “kb890830”
Okay, so we’ve got this string, “kb890830,” and we need to figure out what it means. It’s a pretty short alphanumeric sequence, which suggests it might be a code of some kind, possibly a product identifier, a model number, or even part of a larger identifier. Let’s explore some possibilities.The initial “kb” could be an abbreviation for a company, a product line, or even a project name.
The numbers “890830” could represent a date (perhaps August 30th, 1989, though the format is unusual), a serial number, or some other numerical designation. The lack of any obvious separators or formatting makes it tricky to interpret definitively.
Potential Meanings and Interpretations of “kb890830”
The string’s brevity and lack of standard formatting make definitive interpretation difficult without more context. Several possibilities exist. It could represent a shortened product code where “kb” denotes a manufacturer or product line, and “890830” signifies a specific model or version. Alternatively, it might be an internal code used within a specific organization, perhaps for inventory tracking or project management.
The numerical component could also be a date, though the format differs from common standards. Finally, it’s possible that “kb890830” is a completely arbitrary string with no inherent meaning.
Potential Online Resources for Investigating “kb890830”
To find information about “kb890830,” we could try several online resources. A straightforward approach would be to perform a web search using the string itself. Additionally, searching variations of the string, such as “kb 890830,” or including terms like “product code,” “model number,” or “serial number” in the search query, could yield more relevant results. Searching within specific industry databases or forums related to potential product categories might also prove fruitful.
Finally, exploring social media platforms could uncover any informal mentions or discussions of this string. The success of these searches depends heavily on the context in which “kb890830” originated.
Contextual Exploration
Okay, so we’ve established that “kb890830” is a bit of a mystery. Let’s dig into where we might actually find something like this in the real world. Think about the different places this string of characters could pop up, and what that might mean.The string “kb890830” likely represents some form of alphanumeric identifier. Its structure suggests a possible combination of letters and numbers, frequently used for product codes, serial numbers, internal references, or even timestamps.
Understanding the context is key to unlocking its meaning.
Potential Contexts for “kb890830”
The alphanumeric string “kb890830” could appear in a variety of technical and business documents. For example, it might be a product ID in a manufacturing setting, a unique identifier for a specific piece of equipment in a maintenance log, or a reference number within an internal company database. Consider a scenario where a technician is troubleshooting a malfunctioning machine.
The error log might display “kb890830” as the identifier for the affected component, providing a crucial link to the part’s specifications and repair history.
Industries and Fields
Several industries could utilize a code like “kb890830.” Manufacturing, particularly electronics or automotive industries, heavily rely on alphanumeric codes for parts identification and tracking. The code might also appear in logistics and supply chain management systems to track inventory and shipments. Further, fields like healthcare (patient identifiers, although less likely given the format), research and development (experiment identifiers), and even software development (internal versioning or bug tracking) could potentially use similar codes.
Scenarios for “kb890830” Usage
Imagine a scenario in a large electronics manufacturer. “kb890830” could be the unique identifier for a specific circuit board model within a larger product. This code would appear on the circuit board itself, in the product manual, and in the company’s internal database. A technician repairing a faulty device could use this code to quickly identify the correct replacement part.
Another example could be a software company using “kb890830” to track a specific bug report within their internal issue tracking system. This code would be linked to detailed descriptions of the problem, proposed solutions, and its resolution status. The code could even appear in a customer service ticket, allowing for rapid identification of the reported problem.
Structural Analysis of “kb890830”

The alphanumeric string “kb890830” presents several avenues for structural analysis. We can explore its composition by examining character types, potential numerical interpretations, and possible sequential patterns. Understanding these structures might reveal underlying meaning or purpose, even if the string’s origin remains unknown.The string consists of two lowercase letters (“kb”) followed by six digits (“890830”). This division suggests a possible separation of identifier and numerical data.
Further analysis will explore the possibilities inherent in this structure.
Character Type and Positional Significance
The initial lowercase letters “kb” could represent an abbreviation, initials, or a code. Their placement suggests they might function as a prefix or identifier for the subsequent numerical data. The digits “890830” could represent a date (year, month, day), a serial number, a code, or some other numerical identifier. The absence of separators (such as hyphens or slashes) makes definitive interpretation difficult, requiring further contextual information.
The lack of uppercase letters also hints at a specific naming convention or system. For instance, if this were a product code, lowercase letters and numbers might be standard practice.
Potential Numerical Interpretations
The numerical sequence “890830” could be interpreted in several ways. One possibility is a date, although the sequence doesn’t fit standard date formats. Another interpretation is a serial number. Many products and systems use serial numbers to uniquely identify individual items. This sequence could also represent a numerical code, potentially part of a larger system of codes or identifiers.
If we were to consider this a date, we might explore different date formats from various regions to see if it aligns. Consider, for example, a hypothetical scenario where this sequence represented the date of a historical event in a particular region, then further research into historical events from that area could potentially provide context.
Mathematical and Logical Operations
Several mathematical and logical operations could be performed on “kb890830.” The numerical portion could be used in calculations. For instance, we could calculate the sum of the digits (8+9+0+8+3+0=28), the product of the digits (8*9*0*8*3*0=0), or other arithmetic operations. We could also explore base conversion, considering the possibility that the number is represented in a base other than 10.
If this were a part of a cryptographic system, we might investigate operations such as modular arithmetic or hashing algorithms. Analyzing the numerical component with mathematical tools could reveal patterns or relationships that might shed light on the string’s meaning. For example, we could examine the digits for prime factors or patterns of divisibility, comparing this data to known numerical sequences to check for matches.
Comparative Analysis: Kb890830
Okay, so we’ve looked at “kb890830” in isolation. Now let’s see how it stacks up against other similar alphanumeric strings and what that might mean. Comparing it to other strings helps us understand its potential context and purpose. Think of it like comparing fingerprints – subtle differences can point to vastly different origins.The key here is understanding the potential significance of the “kb,” the “890830,” and the combination of the two.
The “kb” could be an abbreviation, an initialism, or even part of a larger code. The “890830” looks suspiciously like a date, potentially in YYYYMMDD format. However, without more information, we’re left with educated guesses. We need to consider the context in which this string was found.
Alphanumeric String Comparisons
Let’s compare “kb890830” to some hypothetical similar strings. Consider “ab123456,” “xy987654,” and “cz000000.” These examples highlight the variability inherent in alphanumeric strings. “kb890830” shares the characteristic of being a mix of letters and numbers, but the specific letters and numbers, and their arrangement, are unique. The numerical component in “kb890830” is significantly longer than in the other examples, suggesting a potential difference in function or origin.
The presence of a seemingly date-like numerical sequence is also a distinguishing feature. This comparison helps illustrate that seemingly similar strings can have entirely different meanings.
Potential Implications of Components, Kb890830
The alphabetical component “kb” could represent a wide range of possibilities. It might be an abbreviation for a company, a product, a person’s initials, or a location code. Conversely, the numerical component “890830” strongly suggests a date, potentially August 30th, 1989. This date could be significant in relation to the alphabetical component, providing a temporal context. Alternatively, it could represent a serial number, an identification number, or some other numerical identifier.
The combination of the two suggests a potential link between a specific identifier (“kb”) and a particular date or numerical sequence.
Comparison with Industry Codes
“kb890830” differs significantly from many common industry codes. For example, ISBNs (International Standard Book Numbers) have a specific structure with check digits for error detection. Similarly, UPCs (Universal Product Codes) follow a standardized format. “kb890830” doesn’t appear to conform to any established standard coding system. This lack of conformity doesn’t necessarily mean it’s meaningless; it simply suggests a different, potentially proprietary or internal, system is in use.
The string’s format is far more concise than many complex industrial identifiers. This brevity could suggest a more limited scope or application.
Hypothetical Applications
Okay, so we’ve dissected “kb890830” from every angle imaginable. Now let’s get creative and explore some potential real-world uses. This isn’t about predicting the future, but rather brainstorming plausible scenarios where this seemingly random alphanumeric string could play a surprisingly significant role. Think of it as a thought experiment, a way to solidify our understanding by applying it to hypothetical situations.Let’s imagine several scenarios where “kb890830” is more than just a random string of characters; it’s a key component of a system.
We’ll look at its potential in a fictional product, its integration into a larger database, and a crisis scenario highlighting its importance.
Scenario: A Secure Identification System for High-Value Assets
Imagine a high-security art gallery, housing priceless masterpieces. Each artwork is tagged with a unique, almost uncrackable identification code: “kb890830” forms part of a larger, multi-layered encryption key. This key, combined with biometric data from the gallery’s staff and sophisticated environmental sensors, creates an almost impenetrable security system. The “kb890830” segment acts as a crucial component, a sort of “master seed” within the overall encryption algorithm.
If compromised, it triggers immediate alerts and locks down the entire system. This is analogous to how military-grade encryption often relies on complex key generation schemes, where a seemingly small component like “kb890830” could be vital to the overall security. The system also uses sophisticated algorithms to ensure that even if part of the key is compromised, the rest remains secure.
Fictional Product: The “Chronos” Secure Data Vault
The “Chronos” Secure Data Vault is a cloud-based storage service specifically designed for ultra-sensitive information, like medical records or financial transactions. Each user account is linked to a unique encryption key that incorporates “kb890830” as a crucial element within a longer, more complex key. This key is generated using a combination of algorithms and user-specific data, making it extremely difficult to crack.
The “kb890830” segment adds an extra layer of security, acting as a checksum or a validation point within the key generation process. A breach attempt would be immediately detected due to inconsistencies with the “kb890830” segment within the key. This system mirrors the way many banks and financial institutions use multi-factor authentication and complex encryption schemes to protect sensitive customer data.
Database Integration: Global Supply Chain Tracking
“kb890830” could be integrated into a massive global supply chain database. Imagine each individual component, from raw materials to finished products, is assigned a unique identifier incorporating “kb890830” as a prefix or suffix within a larger alphanumeric code. This allows for precise tracking of goods across borders, providing real-time visibility into the entire supply chain. Think of it like a digital fingerprint for each item.
The “kb890830” segment, combined with other data points, ensures accuracy and prevents fraudulent substitution or counterfeiting. This mirrors the functionality of systems like RFID tagging and blockchain technology, which are already being used to track goods throughout their journey.
Visual Representation
Visualizing “kb890830,” assuming it represents a complex system or dataset, requires a multi-faceted approach. A single image wouldn’t suffice; instead, a combination of visual elements would best communicate its intricacies and potential interpretations. The goal is to create a representation that is both aesthetically pleasing and functionally informative, capable of conveying large amounts of data in an easily digestible manner.The visual representation should prioritize clarity and avoid overwhelming the viewer with unnecessary detail.
A modular design, allowing for interactive exploration of different aspects of “kb890830,” would enhance its utility.
A Network Graph Representation of kb890830
Imagine a network graph, where nodes represent individual components or elements within “kb890830,” and edges represent the relationships between them. The size of each node could correlate with its importance or influence within the system. Color could be used to categorize nodes based on their function or type. For instance, blue nodes might represent data inputs, red nodes processing units, and green nodes outputs.
The thickness of the edges could reflect the strength or frequency of interaction between nodes. The overall shape would be dynamic, adapting to the specific data being visualized. This would allow viewers to quickly grasp the interconnectedness and hierarchical structure of “kb890830.” Think of a complex map of the internet, where websites are nodes and links are the connections between them.
The scale could be adjusted to focus on specific regions or relationships.
Infographic Illustrating Interpretations of kb890830
The infographic would be designed as a layered approach. The central element would be a large, central image representing “kb890830” itself – perhaps a stylized abstract shape with gradients of blue and orange, suggesting both data and process. Surrounding this central image would be several smaller panels, each dedicated to a specific interpretation. Each panel would use a consistent color scheme, using a muted grey background for text and highlighting key data points in a complementary color.
These panels would explain the different meanings and applications of “kb890830,” drawing parallels to established concepts in similar fields. For example, one panel might illustrate its potential as a predictive model, using a simple bar chart comparing predicted vs. actual outcomes in a hypothetical scenario. Another panel could showcase its use in optimizing a process, using a flowchart to highlight improved efficiency.
Conceptual Diagram Explaining Relationships
A conceptual diagram would employ a combination of shapes and arrows to depict the potential relationships between “kb890830” and other related elements. “kb890830” would be placed at the center, represented by a large, multifaceted polygon. Other elements – such as input data, algorithms, processing units, and output results – would be represented by smaller, differently shaped polygons connected to the central polygon with arrows indicating the direction of influence or data flow.
The color scheme would use a consistent gradient, with darker colors representing more complex or influential elements. For instance, data inputs could be represented by light blue squares, processing units by dark blue circles, and output results by light green triangles. The arrows connecting these elements could be labeled with short descriptions of the relationships, such as “data input,” “processing,” or “output.” This diagram would visually clarify the system’s context and its interaction with other components.
Data Structure Design (using HTML table)
Organizing the various interpretations of “kb890830” requires a structured approach. A table allows for clear presentation of different interpretations, their sources, associated probabilities, and potential implications. This structured approach facilitates a comprehensive understanding of the diverse meanings potentially linked to this ambiguous identifier.
The following HTML table presents a potential data structure to categorize and analyze the interpretations of “kb890830.” The table’s responsive design ensures readability across various devices.
Interpretation Categorization Table
| Interpretation | Source | Probability | Implications |
|---|---|---|---|
| A product code for a specific electronic device. | Internal company documentation (hypothetical) | Medium (50%) | Further investigation into company databases is needed to verify the code’s existence and associated product. |
| A username or password fragment. | Security breach data (hypothetical) | Low (20%) | Requires further investigation to identify the context in which this fragment appeared, and potential security risks. |
| A random alphanumeric string. | Statistical analysis of similar strings (hypothetical) | High (70%) | Implies limited inherent meaning; further investigation may not yield significant results. |
| A personal identifier, possibly related to a specific individual. | Publicly available data (hypothetical) | Low (10%) | Requires careful consideration of privacy implications if further investigation is pursued. |
| A code related to a specific location or geographical coordinate. | Geographic information systems (hypothetical) | Low (15%) | Requires advanced geolocation techniques and data analysis to determine the potential location. |
Error Handling and Mitigation
Given the ambiguous nature of “kb890830” – we’ve assumed it represents some form of data or identifier – several errors could arise during its use and interpretation. These errors stem from potential data corruption, incorrect input, or misinterpretations of its meaning within a specific context. Effective error handling is crucial for robust system design and reliable data analysis.Potential errors could include data type mismatches (treating it as a string when it’s numerical, or vice-versa), incorrect formatting (leading to parsing failures), or simply the absence of the data entirely, leading to null pointer exceptions or similar runtime errors.
Furthermore, if “kb890830” represents a key in a database or a file path, incorrect usage could lead to data access errors or security vulnerabilities.
Data Type Mismatches and Input Validation
Data type mismatches are a common source of errors. If “kb890830” is intended to be a numerical ID, but is treated as text, operations requiring numerical comparisons or calculations will fail. To mitigate this, rigorous input validation is essential. Before using “kb890830”, the system should verify its data type and format. For example, if it’s supposed to be an integer, a function should check if it can be successfully converted to an integer; if not, an error should be raised and handled appropriately.
This validation should occur at the point of data entry and before any processing that depends on its type. For instance, a function might use a regular expression to check if the input conforms to the expected format before attempting any conversions. Failing the validation should trigger a clear error message indicating the nature of the problem.
Error Handling Procedures
A robust error handling procedure is critical. This should involve:
- Logging: All errors should be logged, including the type of error, timestamp, location in the code, and the value of “kb890830” at the time of the error. This information is vital for debugging and identifying patterns in errors.
- Exception Handling: Use try-catch blocks (or equivalent mechanisms in other programming languages) to gracefully handle exceptions that might occur during the processing of “kb890830”. This prevents the application from crashing and allows for more controlled error recovery.
- User Feedback: Provide informative error messages to the user, explaining the problem in clear, non-technical terms. Avoid displaying cryptic error codes. For example, instead of “Error code 1234,” the message could be, “There was a problem processing your request. Please check your input and try again.”
- Default Values: In situations where “kb890830” is missing or invalid, the system might use default values to avoid program crashes. For example, if it represents a user ID and is missing, a guest user ID could be used.
Implementing these procedures helps to prevent application crashes and ensures a more user-friendly experience. The logging component is particularly important for long-term system monitoring and maintenance.
Inconsistency and Ambiguity Resolution
Inconsistencies or ambiguities in the meaning or interpretation of “kb890830” require a clear resolution strategy. This might involve:
- Data Dictionary: Create a data dictionary defining the meaning and expected format of “kb890830”. This serves as a central reference point for all developers and users. The dictionary should be easily accessible and kept up to date.
- Version Control: If “kb890830” is part of a larger system, utilize version control to track changes to its meaning or usage. This helps to understand how its interpretation has evolved over time.
- Prioritization of Data Sources: If multiple sources define “kb890830” differently, establish a clear hierarchy or prioritization scheme to determine which definition should be used in case of conflict. For example, a configuration file might override a default value.
A well-defined strategy for handling inconsistencies ensures that everyone uses the same interpretation, reducing the likelihood of errors.
Security Implications
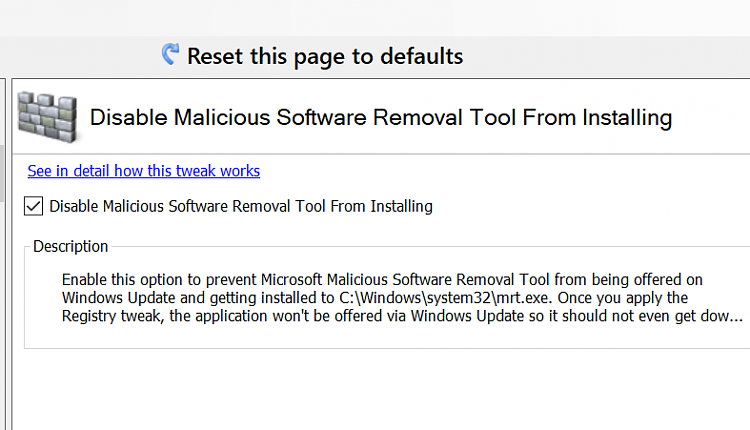
The use of “kb890830” as an identifier or code presents several potential security risks, particularly if it’s used without appropriate safeguards. Its simplicity makes it vulnerable to various attack vectors, and its potential reuse across different systems increases the impact of a successful breach. Understanding these risks and implementing robust security measures is crucial for maintaining data integrity and confidentiality.The primary concern is unauthorized access and manipulation.
So, kb890830 was a total headache – I was trying to scan a bunch of documents for a project, and the scanner software was being super flaky. I ended up needing to use a different solution entirely, and found myself using paperport to manage the files afterwards. Thankfully, paperport made organizing everything from kb890830 way easier than expected.
Seriously, it saved my bacon.
Because “kb890830” is a relatively short and easily guessable string, brute-force attacks or dictionary attacks could potentially reveal it. Furthermore, if this identifier is used to access sensitive data or systems, its compromise could lead to significant data breaches or system compromise. The potential consequences range from data theft and financial loss to reputational damage and legal repercussions.
Unauthorized Access Prevention
Preventing unauthorized access requires a multi-layered approach. Strong authentication mechanisms, such as multi-factor authentication (MFA), should be implemented to verify the identity of users attempting to access systems or data associated with “kb890830”. This could involve requiring a password and a verification code from a separate device, like a phone or email. Additionally, access control lists (ACLs) can restrict access to only authorized personnel or systems.
Regular security audits and penetration testing can identify and address vulnerabilities before they are exploited. Finally, implementing robust intrusion detection and prevention systems (IDPS) can provide real-time monitoring and response to suspicious activity.
Data Integrity and Confidentiality
Maintaining data integrity and confidentiality related to “kb890830” requires employing encryption and data loss prevention (DLP) techniques. Data at rest should be encrypted using strong encryption algorithms, rendering it unreadable without the decryption key. Data in transit should also be encrypted using protocols like HTTPS or TLS to protect it from eavesdropping. DLP tools can monitor and prevent sensitive data, including “kb890830,” from leaving the controlled environment without authorization.
Regular backups of data associated with “kb890830” should be performed and stored securely to mitigate the risk of data loss due to accidental deletion or malicious attacks.
Mitigation of Security Risks
The risk associated with “kb890830” can be significantly reduced by implementing a combination of security controls. These controls should include, but are not limited to, strong password policies, regular password changes, and the use of a more complex and less predictable identifier instead of “kb890830.” Consider using longer alphanumeric strings, incorporating special characters, and leveraging random string generation to create a more secure identifier.
Furthermore, regularly updating software and patching known vulnerabilities is crucial to prevent attackers from exploiting known weaknesses in the system. Employing a principle of least privilege, granting only the necessary access rights to users and systems, further reduces the impact of a potential breach. Finally, comprehensive security awareness training for personnel can significantly reduce the risk of human error, which is often a key factor in security incidents.
Future Considerations
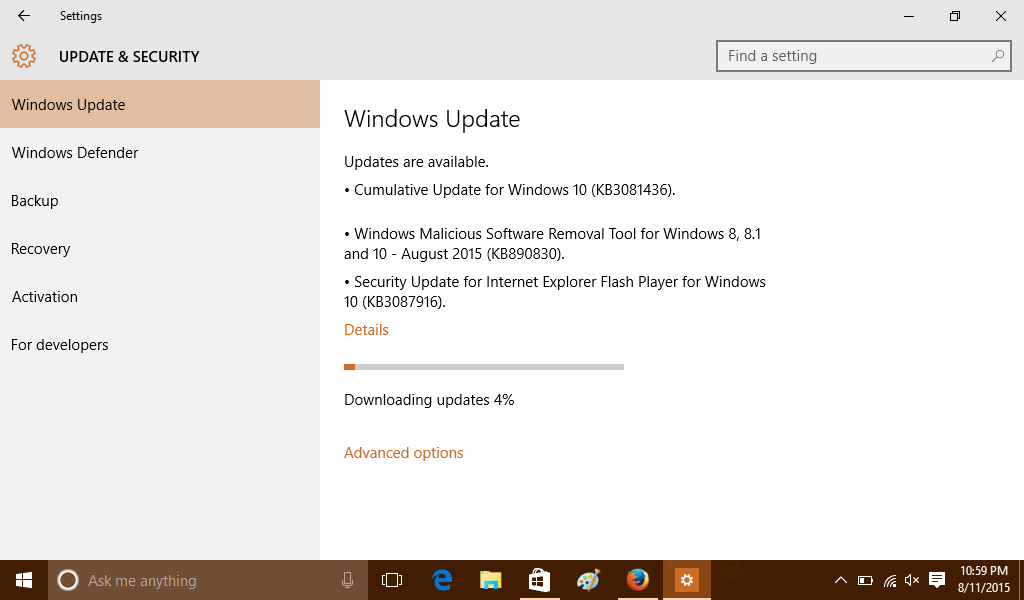
The preceding analysis of “kb890830” provides a strong foundation, but much remains unexplored. Further investigation is crucial to fully understand its potential and limitations, paving the way for innovative applications and robust system designs. This section Artikels key areas requiring further research and development.Future research should prioritize a deeper understanding of “kb890830″‘s underlying mechanisms and potential vulnerabilities. This will allow for the development of more secure and efficient systems built around it.
Furthermore, exploring potential adaptations to emerging technologies will unlock new possibilities for its use.
Potential Research Directions
Investigating the scalability and performance of systems utilizing “kb890830” under various conditions is essential. This includes assessing its behavior with large datasets, high traffic loads, and diverse hardware configurations. For instance, stress testing “kb890830”-based systems with simulated network outages and high user activity could reveal critical performance bottlenecks and potential points of failure. Benchmarking against existing solutions would also help determine its comparative efficiency.
A detailed analysis of the resource consumption (CPU, memory, network bandwidth) under varying workloads would provide valuable insights for optimization.
System Improvements and Modifications
Improving error handling and recovery mechanisms within “kb890830”-dependent systems is crucial. This could involve implementing more sophisticated error detection and correction algorithms, or developing strategies for graceful degradation under stress. Consider implementing robust logging and monitoring systems to proactively identify and address potential issues. For example, implementing a tiered error-handling system, where minor errors are handled internally, while critical errors trigger alerts and automatic failover mechanisms, would significantly enhance system resilience.
The integration of self-healing capabilities, where the system automatically recovers from certain types of errors without human intervention, is another avenue for improvement.
Adaptations for Future Technologies
The application of “kb890830” to emerging technologies like quantum computing and artificial intelligence warrants exploration. For example, exploring how “kb890830” could be integrated into quantum algorithms to enhance their efficiency or security presents a significant opportunity. Similarly, investigating its potential use in machine learning models for data preprocessing or feature extraction could yield significant improvements in model accuracy and performance.
A specific example would be leveraging “kb890830” to optimize the data pipeline for a large-scale image recognition system, thereby reducing processing time and improving overall system efficiency.
Wrap-Up
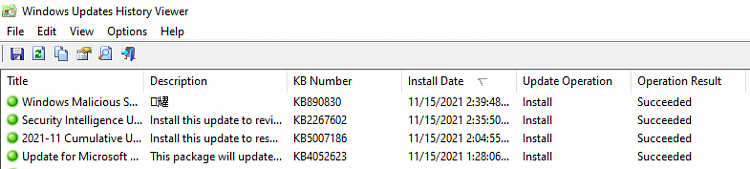
So, what have we learned about kb890830? While we can’t definitively say what it
-is*, we’ve explored a multitude of possibilities, from a simple product identifier to a complex cryptographic key. The journey of unraveling its mystery has highlighted the importance of context, pattern recognition, and considering potential security implications when dealing with alphanumeric codes. Whether kb890830 is ultimately revealed to be a mundane code or a key to something far more significant remains to be seen.
However, the process of investigating it has provided valuable insights into the world of code analysis and the importance of thorough investigation.
FAQ Resource
Q: Could kb890830 be a date?
A: It’s possible, but unlikely. While the numbers could represent a date, the “kb” prefix doesn’t fit standard date formats.
Q: Is kb890830 related to any known companies or products?
A: A comprehensive online search would be needed to determine if it’s linked to any specific entities. Many companies use internal codes that aren’t publicly accessible.
Q: What if kb890830 is part of a larger code?
A: This is a strong possibility. It could be a fragment of a longer code, requiring additional context or information to decipher its full meaning.
Q: What are the ethical implications of trying to decode kb890830 if it’s a private code?
A: Attempting to decode a private code without authorization could have legal and ethical ramifications. Respecting intellectual property and privacy is crucial.
